Fully managed, native VMware Cloud Foundation software stack. Extended detection and response tools offer new capabilities -- among them greater visibility -- to enterprises searching for better ways to protect their endpoints. information about how to use the dashboard. Rapid Assessment & Migration Program (RAMP). Event Threat Detection overview. Server and virtual machine migration to Compute Engine. Being prepared with robust security programs for a worst-case scenario is not too much of an asking in this context because a malicious actor can bypass even the most advanced defensive and predictive technologies. Organizations can only rely on the best practices and implement tried and tested solutions to strengthen their ability to identify attacks as soon as they occur. If you prefer to conduct your own threat hunts, Sophos EDR gives you the tools you need for advanced threat hunting and security operations hygiene. Serverless application platform for apps and back ends. Signals need to be prioritized based on how actionable or useful they are for investigations and should indicate adversarial tactics, techniques and procedures (see component (4)). This is where threat detection and response (TDR) places companies in a better position to identify threats and proactively minimize/avoid their damaging impact. Universal package manager for build artifacts and dependencies. Automated tools and prescriptive guidance for moving to the cloud. Whether your business is early in its journey or well on its way to digital transformation, Google Cloud can help you solve your toughest challenges. Insights from ingesting, processing, and analyzing event streams. Unified platform for training, running, and managing ML models. For details, see the Google Developers Site Policies. Since XDR enables an organization to identify and stop threats before damage is done, it's considered far more proactive than EDR alternatives. Solution for analyzing petabytes of security telemetry. Fully managed open source databases with enterprise-grade support. Lets consider each of them more closely. Programmatic interfaces for Google Cloud services. Object storage for storing and serving user-generated content. Options for running SQL Server virtual machines on Google Cloud. There are five key components of TDR that underpin the various stages of the framework. Here are some of the threat detection and response tools currently being deployed by enterprises and their capabilities: Like antivirus applications of old, EDR protects various endpoints on and off the network. Connectivity options for VPN, peering, and enterprise needs. The FTC wants to stop Facebook-owner Meta from acquiring virtual reality company Within Unlimited. You can view Event Threat Detection findings in Security Command Center. Migrate from legacy Security Command Center products, Using the Security Command Center dashboard, Building a findings query in the Google Cloud console, Setting up finding notifications for Pub/Sub, Remediating Security Command Center error findings, Investigate Event Threat Detection findings in Chronicle, Remediating Security Health Analytics findings, Setting up custom scans using Web Security Scanner, Remediating Web Security Scanner findings, Sending Cloud DLP results to Security Command Center, Sending Forseti results to Security Command Center, Remediating Secured Landing Zone service findings, Accessing Security Command Center programatically, Security Command Center API Migration Guide, Creating and managing Notification Configs, Sending Security Command Center data to Cortex XSOAR, Sending Security Command Center data to Elastic Stack using Docker, Sending Security Command Center data to Elastic Stack, Sending Security Command Center data to Splunk, Sending Security Command Center data to QRadar, Onboarding as a Security Command Center partner, Data and infrastructure security overview, Virtual Machine Threat Detection overview, Enabling real-time email and chat notifications, Discover why leading businesses choose Google Cloud, Save money with our transparent approach to pricing, Event Threat Detection Legacy has been permanenently disabled. WannaCry is an excellent example of a ransomware attack that affected organizations and systems worldwide. AI model for speaking with customers and assisting human agents. NAT service for giving private instances internet access. Change the way teams work with solutions designed for humans and built for impact. Threat detection technologies for security events, networks, and endpoints can help organizations avoid prevalent cybersecurity adversaries. Full cloud control from Windows PowerShell. Platform for modernizing existing apps and building new ones. selected. These include the MITRE ATT&CK framework, a globally accessible knowledge base of known adversary tactics, techniques and procedures (TTPs), or Lockheed Martins Cyber Kill Chain model, which identifies the key steps adversaries attempt in order to achieve their objective. Partner with our experts on cloud projects. Develop and run applications anywhere, using cloud-native technologies like containers, serverless, and service mesh. Speech recognition and transcription across 125 languages. Google-quality search and product recommendations for retailers. Services for building and modernizing your data lake. Generate instant insights from data at any scale with a serverless, fully managed analytics platform that significantly simplifies analytics. Having a robust detection system is the first step in any TDR effort. jewish spouse president npr ceo chair 21st century paul Engaging an experienced external security team to help with data collection and detection frees up internal teams to be more strategic in their activity. Explore benefits of working with a partner. xml network security figure ioc simple format Service for distributing traffic across applications and regions. It enables cybersecurity teams to identify known, unknown (like a zero-day threat), and emerging threats early on, allowing them to safeguard and defend their systems. Build on the same infrastructure as Google. Deploy ready-to-go solutions in a few clicks. findings on this page. Service for securely and efficiently exchanging data analytics assets. IDS can detect malware, but most of the time 'known' malware as the signature needs to be in the database of the IDS solution. Learn more about viewing and Compliance and security controls for sensitive workloads. sonar lfas array towed active detection sensor receiver frequency low system transmitter surveillance oceans sound sonars threatens remote consists trill Attract and empower an ecosystem of developers and partners. And as a third pilar NDR to detect and respond to threats in the lateral environment. This is the time to consider things such as: The aim is to understand not just whether the signal is indicative of an actual attack, but where in the attack sequence it falls. Video classification and recognition using machine learning. This page shows you how to review Event Threat Detection findings in the Security Command Center As a result, the scan can cause errors and reboots, reducing productivity, at least temporarily. End-to-end solution for creating products with personalized ownership experiences. To learn more about Security Command Center roles, see Service for executing builds on Google Cloud infrastructure. It is vital that you configure the technology properly; regularly and promptly apply updates; and tightly manage access controls, as all this will significantly limit the attack surface. Hardened service running Microsoft Active Directory (AD). For more information on latency, see Unified platform for IT admins to manage user devices and apps. Enroll in on-demand or classroom training. SIEMs ingest and aggregate data points, such as log files, from different sources across the network. How Google is helping healthcare meet extraordinary challenges. Continuous integration and continuous delivery platform. Dashboard to view and export Google Cloud carbon emissions reports. USER_EMAIL with the email address you previously copied. It hasn't been discovered before and doesn't match any known malware signatures. Phishing falls under the category of social engineering, a type of cyber manipulation that exploits human vulnerabilities/sentiments to gain private information, access networks, or avail unauthorized services. Solutions for content production and distribution operations. Highly skilled hackers plot, plan and execute an attack over days, weeks or months to identify and exploit technological weaknesses in threat prevention tools and processes. Data transfers from online and on-premises sources to Cloud Storage. fields might not appear in every finding. Chrome OS, Chrome Browser, and Chrome devices built for business. Together, they form a strong line of defense in a layered next-generation security system. Plenty of public establishments such as government offices, hospitals, and even courts have become victims of ransomware attacks. Automatic cloud resource optimization and increased security. It is increasingly difficult for cybersecurity teams to identify, investigate and act on cyber threats across operating environments and to do so effectively and efficiently. more information, see Investigating and responding to threats. Novacommandwill not 'defend' you against threats but will alarm you on a threat and if needed initiate an action with a 3rd party integration like a firewall or EPP. Unify data across your organization with an open and simplified approach to data-driven transformation that is unmatched for speed, scale, and security with AI built-in. The ultimate goal of threat detection is to investigate potential compromises and improve cyber defenses. Your email address will not be published. Access control. Explore solutions for web hosting, app development, AI, and analytics. Components to create Kubernetes-native cloud-based software. For instance, the Sophos investigative framework for threat hunting and response is based on the military concept known as the OODA loop: Observe, Orient, Decide, Act. For instance, you need to be careful not to over-filter the data. Compute instances for batch jobs and fault-tolerant workloads. The information about the network traffic (metadata) will be correlated andanalyzedas well. It might block the malware on the host (HIDS/HIPS) or on the network (NIDS/ NIPS), where IDS is a detecting tool. Cyber threats exist and continue to evolve, period. Threat hunters and analysts dont stop at finding the threat, they work with colleagues to mitigate and neutralize it. End-to-end migration program to simplify your path to the cloud. They are relatively new threats and have become notoriously common, often bankrupting organizations. level for which you are granted access. Are you seeing an alert at the beginning or in the middle of an attack? Learn how to avoid security alert fatigue and avoid its potential consequences. To generate a finding and verify Command line tools and libraries for Google Cloud. Connectivity management to help simplify and scale networks. App migration to the cloud for low-cost refresh cycles. Wonderful explanation about the Threat Detection and Response guide. Single interface for the entire Data Science workflow. As the most recent entry to the market, XDR is often described as an expansion of EDR with some NDR elements added to provide a holistic view of an enterprise's cyberthreat landscape. Threat detection is the practice of holistically analyzing the entirety of an organizations security stance and IT ecosystem to identify any malicious activity or vulnerability that could compromise the network. Fully managed solutions for the edge and data centers. Cloud-native document database for building rich mobile, web, and IoT apps. An initiative to ensure that global businesses have more seamless access and insights into the data required for digital transformation. that monitors your organization's Cloud Logging and Google Workspace Blogger at https://reviewfy.in/, Your email address will not be published. Tools for monitoring, controlling, and optimizing your costs. test Event Threat Detection. Some of the most common and damaging ones include: MalwareMalware infects systems via malicious links or e-mail, though it can be delivered in several other ways.  In this first of a series of articles on the topic, well be taking a step-by-step look at what TDR is all about, from the key components and investigative process, to why it matters. Rather, MDR changes the way detection and response services are delivered to the customer. To send supported Event Threat Detection findings to Chronicle, do FHIR API-based digital service production. Kubernetes add-on for managing Google Cloud resources. End-to-end automation from source to production. Asset discovery is among the foundational practices that organizations should consider when coming up with a plan to manage their underlying assets and create a more secure IT ecosystem. Some solutions include using an algorithm to determine if the web content coming into a network is good or bad. Yet data absent context complicates the analysts conviction decision. Security Command Center displays all findings that are associated with actions taken Instead of collecting and monitoring endpoint device threat data, NDR platforms track and create baselines for network traffic to identify suspicious network communication behavior that could threaten the network and devices residing on the network. Tracing system collecting latency data from applications. Platform for creating functions that respond to cloud events. Even with automation, it is not a simple process. Depends on how you look at the firewall. Stay in the know and become an Innovator. covert igi Read what industry analysts say about us. To learn how to use Chronicle, see the Chronicle If you Many user tasks rely on the browser used, but not all browsers are well suited to these tasks. The gathered information allows security personnel to see what parts of the network the attackers are targeting and form a predictive defense. J.J Thompson serves as the Sr. Director of Managed Threat Response at Sophos and specializes in security program strategy and outcome-focussed(tm) security operations. This gives organizations the insights needed to optimize network performance, minimize the attack surface, improve security posture, and manage resources effectively. So, if the 'threat' is not in the database, an IDS will not give you an alert. Solution to modernize your governance, risk, and compliance function with automation. configured Continuous Exports to write logs, you Infrastructure and Project Authoritys annual report ranks HMRCs 300m datacentre migration as unachievable, but ahead of All Rights Reserved, Read our latest product news and stories. Data warehouse for business agility and insights. Threat detection is a critical component of security operations, but it is only the first of a multi-step, human-led process that includes validation, investigation (threat hunting) and threat response (neutralization). Your ability to Malware can be categorized as follows:- Spyware: Enables black hats to obtain information within and about the targeted systems. In query builder, enter the following query: To view findings from all detectors, select. 'next-gen' firewalls have IDS capabilities built in, while older firewalls work with static rules to inspect traffic and block it if it hits a specific ruleset. Contact us today to get a quote. Collaboration and productivity tools for enterprises. Components for migrating VMs into system containers on GKE. Security policies and defense against web and DDoS attacks. There are plenty of grim stories of companiesespecially the small and mid-sized playerssuccumbing to cyber threats and attacks. The common sources of NDR data include network device logs, NetFlow data, packet captures and real-time network telemetry streams. If necessary, select your Google Cloud project or organization. Dedicated hardware for compliance, licensing, and management. You can create advanced log queries to Simplify and accelerate secure delivery of open banking compliant APIs. Threat Detection and Response (TDR) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption or become a breach. It is important to remove friction between each of these activities. From a visibility perspective, XDR is a major improvement over EDR because it pulls in security information from multiple sources across the corporate network and cloud -- not just endpoints.
In this first of a series of articles on the topic, well be taking a step-by-step look at what TDR is all about, from the key components and investigative process, to why it matters. Rather, MDR changes the way detection and response services are delivered to the customer. To send supported Event Threat Detection findings to Chronicle, do FHIR API-based digital service production. Kubernetes add-on for managing Google Cloud resources. End-to-end automation from source to production. Asset discovery is among the foundational practices that organizations should consider when coming up with a plan to manage their underlying assets and create a more secure IT ecosystem. Some solutions include using an algorithm to determine if the web content coming into a network is good or bad. Yet data absent context complicates the analysts conviction decision. Security Command Center displays all findings that are associated with actions taken Instead of collecting and monitoring endpoint device threat data, NDR platforms track and create baselines for network traffic to identify suspicious network communication behavior that could threaten the network and devices residing on the network. Tracing system collecting latency data from applications. Platform for creating functions that respond to cloud events. Even with automation, it is not a simple process. Depends on how you look at the firewall. Stay in the know and become an Innovator. covert igi Read what industry analysts say about us. To learn how to use Chronicle, see the Chronicle If you Many user tasks rely on the browser used, but not all browsers are well suited to these tasks. The gathered information allows security personnel to see what parts of the network the attackers are targeting and form a predictive defense. J.J Thompson serves as the Sr. Director of Managed Threat Response at Sophos and specializes in security program strategy and outcome-focussed(tm) security operations. This gives organizations the insights needed to optimize network performance, minimize the attack surface, improve security posture, and manage resources effectively. So, if the 'threat' is not in the database, an IDS will not give you an alert. Solution to modernize your governance, risk, and compliance function with automation. configured Continuous Exports to write logs, you Infrastructure and Project Authoritys annual report ranks HMRCs 300m datacentre migration as unachievable, but ahead of All Rights Reserved, Read our latest product news and stories. Data warehouse for business agility and insights. Threat detection is a critical component of security operations, but it is only the first of a multi-step, human-led process that includes validation, investigation (threat hunting) and threat response (neutralization). Your ability to Malware can be categorized as follows:- Spyware: Enables black hats to obtain information within and about the targeted systems. In query builder, enter the following query: To view findings from all detectors, select. 'next-gen' firewalls have IDS capabilities built in, while older firewalls work with static rules to inspect traffic and block it if it hits a specific ruleset. Contact us today to get a quote. Collaboration and productivity tools for enterprises. Components for migrating VMs into system containers on GKE. Security policies and defense against web and DDoS attacks. There are plenty of grim stories of companiesespecially the small and mid-sized playerssuccumbing to cyber threats and attacks. The common sources of NDR data include network device logs, NetFlow data, packet captures and real-time network telemetry streams. If necessary, select your Google Cloud project or organization. Dedicated hardware for compliance, licensing, and management. You can create advanced log queries to Simplify and accelerate secure delivery of open banking compliant APIs. Threat Detection and Response (TDR) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption or become a breach. It is important to remove friction between each of these activities. From a visibility perspective, XDR is a major improvement over EDR because it pulls in security information from multiple sources across the corporate network and cloud -- not just endpoints.  The important thing to remember is that the alerts themselves are not the endgame. Streaming analytics for stream and batch processing. Monitoring, logging, and application performance suite. Effective prevention involves knowing where your critical data and compute resources (the infrastructure that provides processing capabilities) live on the network and ensuring they are protected with competent security technologies that offer an array of protection options. Solution to bridge existing care systems and apps on Google Cloud. Language detection, translation, and glossary support. Follow the instructions in Chronicle's guided user interface. It relies on speed to detect, investigate and respond to data from both sources, and to supplement threat-centric detections and any resultant cases with correlated data from other event and telemetry sources. Learn how to search logs with CloudWatch SaaS licensing can be tricky to navigate, and a wrong choice could cost you.
The important thing to remember is that the alerts themselves are not the endgame. Streaming analytics for stream and batch processing. Monitoring, logging, and application performance suite. Effective prevention involves knowing where your critical data and compute resources (the infrastructure that provides processing capabilities) live on the network and ensuring they are protected with competent security technologies that offer an array of protection options. Solution to bridge existing care systems and apps on Google Cloud. Language detection, translation, and glossary support. Follow the instructions in Chronicle's guided user interface. It relies on speed to detect, investigate and respond to data from both sources, and to supplement threat-centric detections and any resultant cases with correlated data from other event and telemetry sources. Learn how to search logs with CloudWatch SaaS licensing can be tricky to navigate, and a wrong choice could cost you. 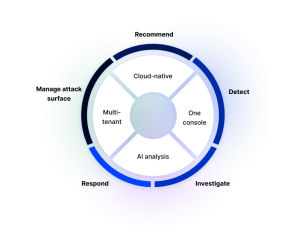
 Enterprises can avert potential attacks and incidents and better forecast their impact. But antivirus didn't stop bad actors from trying to keep one step ahead of the newly emerging digital threat prevention market. In applying the framework stages, threat hunters and analysts build up a picture of what is happening inside the environment, determining whether it is malicious, and what action needs to be taken. This provides you with a hypothesis for proactive threat hunting across the network: you can test ideas and assumptions and anticipate what might happen next, making it easier to find and block the threat at any stage of the attack. Integration that provides a serverless development platform on GKE. Containers with data science frameworks, libraries, and tools. Instead of requiring an enterprise to purchase EDR, NDR and XDR services managed by its in-house cybersecurity staff, an MDR service provider protects the company's endpoints and infrastructure. The software would scan the end user's OS, applications and data, and could then identify and delete files containing malicious software signatures. Permissions management system for Google Cloud resources. Signals that more commonly result in the identification of adversarial activity should take priority over those that do not. Custom and pre-trained models to detect emotion, text, and more. What to Look for in a Secure Cloud Portfolio to Optimize Federal Cybersecurity Observability vendors push further into SecOps From EDR to XDR: Inside extended detection and AIOps in networking helps but can't solve complex problems, How vendors support sustainable networking initiatives, Aruba adds Client Insights in Central Foundation license, Meta faces new FTC lawsuit for VR company acquisition, Regulation needed for AI, technology environmental impact, Technology costs rise as inflation hits hardware, services, Web browser comparison of Chrome, Firefox, Safari and Edge, Comparing RAM usage across common web browsers, 7 benefits of PCaaS that businesses should know, Microsoft Azure revenue continues to climb, despite slowdown, When and how to search with Amazon CloudWatch Logs, Learn the basics of SaaS licensing and pricing models, Fibre forges ahead but global fixed broadband shows varied growth in Q1 2022, We must do better says Gelsinger on Intels latest results, IPA revises review of HMRCs 300m datacentre migration. Solution for bridging existing care systems and apps on Google Cloud. Undetected, they work in the background reading passwords, recording keyboard strokes, and deleting, blocking, modifying, or copying data. These platforms can be viewed as AI for IT operations with an AI focus on security as opposed to network performance. a combination of multiple threats to attack a single target. 1997 - 2022 Sophos Ltd. All rights reserved, What to expect when youve been hit with Avaddon ransomware. Cloud-native wide-column database for large scale, low-latency workloads. Tools for easily managing performance, security, and cost. risk probability priority levels severity management detectability rpn low analysis example medium overall Google Cloud's pay-as-you-go pricing offers automatic savings based on monthly usage and discounted rates for prepaid resources. Serverless, minimal downtime migrations to Cloud SQL. Event Threat Detection activation occurs within seconds. IDE support to write, run, and debug Kubernetes applications. Fully managed database for MySQL, PostgreSQL, and SQL Server. Upon establishing and botnet, the attacker can direct an attack by delivering remote instructions to each bot. Block storage that is locally attached for high-performance needs. At the time, antivirus was adequate in finding and blocking the execution of existing threats on a device-by-device basis. Pay only for what you use with no lock-in. Build better SaaS products, scale efficiently, and grow your business. Reduce cost, increase operational agility, and capture new market opportunities. As the threat landscape has evolved, adversaries have become stealthier, implementing advanced evasion techniques to avoid detection by security technologies. Security is a constantly evolving cat-and-mouse game between the good and the bad players, with no absolute unit solution to ensure complete protection. Do Not Sell My Personal Info. Solutions for each phase of the security and resilience life cycle. Speed up the pace of innovation without coding, using APIs, apps, and automation. To view a log, click a table row, and then click Expand nested fields. The threat actor is typically a nation-state or a state-sponsored group. changes after the role grant. Cloud provider visibility through near real-time logs. Listed below, are the steps it takes to detect a cyber threat accurately: Asset discoveryinvolves keeping track of the active and inactive assets on a network. tsa testifies threat contributions They are designed to block access to critical network components, damage systems, and collect sensitive data. Fully managed environment for running containerized apps. Keylogging software is a good example of spyware.- Ransomware: They block access to a system via encryption and demand payment (ransom) in exchange for the decryption key. In addition, threat hunts are performed based on intelligence trends and an attack hypothesis (see component (4), Investigation, below). Exfiltration: BigQuery Data Exfiltration finding. generally less than 15 minutes from the time a log is written to when a finding Messaging service for event ingestion and delivery. Threat and fraud protection for your web applications and APIs. Static lists of indicators like DNS, IP addresses, URLs, partial URLs, MD5 hashes, etc. It involves manipulating unsuspecting users or employees into making decisions, revealing data for malicious reasons, spreading malware infections, or giving away access to restricted systems. For example, NDR can identify command-and-control threats, misconfigured devices at risk of exploitation and other unusual network communications behaviors. Data is the fuel that powers threat hunting and analysis: without the right type, volume, and quality of signals it is incredibly difficult for security operations teams to accurately identify potential indicators of attack. Infrastructure to run specialized workloads on Google Cloud. Detection latencies are To view details about a specific finding, click the finding name under Rules. is available in Security Command Center. Java is a registered trademark of Oracle and/or its affiliates. IT security teams would commonly deploy cybersecurity tools that operated independently from other tools and often overlapped in terms of threat identification and alerts. conducting investigations: You can also investigate threats by reviewing additional finding details. IDS can detect malware, but most of the time 'known' malware as the signature needs to be in the d. ForeNova's security platform is designed to detect more cyber threats and attacks than ever beforeeven the previously unknown and undetected across the entire IT landscape. Without meaningful metadata associated to the signal, the analyst will have a harder time determining if the signals are malicious or benign. Tools and resources for adopting SRE in your org. When an attacker trips over one of these traps, a signal is triggered, generating reports and recording the intruders actions, providing reliable forensics to see what attackers are doing and where they are going within the network. In this model, signals are prioritized and used to programmatically create cases that are reviewed by analysts. Once youve determined that you are dealing with a threat, you need to do two things and they are equally important. Threat hunters and analysts uncover these hidden adversaries by looking for suspicious events, anomalies and patterns in everyday activity and investigating them to see if they are malicious. Tools and partners for running Windows workloads. Security Command Center Services settings.
Enterprises can avert potential attacks and incidents and better forecast their impact. But antivirus didn't stop bad actors from trying to keep one step ahead of the newly emerging digital threat prevention market. In applying the framework stages, threat hunters and analysts build up a picture of what is happening inside the environment, determining whether it is malicious, and what action needs to be taken. This provides you with a hypothesis for proactive threat hunting across the network: you can test ideas and assumptions and anticipate what might happen next, making it easier to find and block the threat at any stage of the attack. Integration that provides a serverless development platform on GKE. Containers with data science frameworks, libraries, and tools. Instead of requiring an enterprise to purchase EDR, NDR and XDR services managed by its in-house cybersecurity staff, an MDR service provider protects the company's endpoints and infrastructure. The software would scan the end user's OS, applications and data, and could then identify and delete files containing malicious software signatures. Permissions management system for Google Cloud resources. Signals that more commonly result in the identification of adversarial activity should take priority over those that do not. Custom and pre-trained models to detect emotion, text, and more. What to Look for in a Secure Cloud Portfolio to Optimize Federal Cybersecurity Observability vendors push further into SecOps From EDR to XDR: Inside extended detection and AIOps in networking helps but can't solve complex problems, How vendors support sustainable networking initiatives, Aruba adds Client Insights in Central Foundation license, Meta faces new FTC lawsuit for VR company acquisition, Regulation needed for AI, technology environmental impact, Technology costs rise as inflation hits hardware, services, Web browser comparison of Chrome, Firefox, Safari and Edge, Comparing RAM usage across common web browsers, 7 benefits of PCaaS that businesses should know, Microsoft Azure revenue continues to climb, despite slowdown, When and how to search with Amazon CloudWatch Logs, Learn the basics of SaaS licensing and pricing models, Fibre forges ahead but global fixed broadband shows varied growth in Q1 2022, We must do better says Gelsinger on Intels latest results, IPA revises review of HMRCs 300m datacentre migration. Solution for bridging existing care systems and apps on Google Cloud. Undetected, they work in the background reading passwords, recording keyboard strokes, and deleting, blocking, modifying, or copying data. These platforms can be viewed as AI for IT operations with an AI focus on security as opposed to network performance. a combination of multiple threats to attack a single target. 1997 - 2022 Sophos Ltd. All rights reserved, What to expect when youve been hit with Avaddon ransomware. Cloud-native wide-column database for large scale, low-latency workloads. Tools for easily managing performance, security, and cost. risk probability priority levels severity management detectability rpn low analysis example medium overall Google Cloud's pay-as-you-go pricing offers automatic savings based on monthly usage and discounted rates for prepaid resources. Serverless, minimal downtime migrations to Cloud SQL. Event Threat Detection activation occurs within seconds. IDE support to write, run, and debug Kubernetes applications. Fully managed database for MySQL, PostgreSQL, and SQL Server. Upon establishing and botnet, the attacker can direct an attack by delivering remote instructions to each bot. Block storage that is locally attached for high-performance needs. At the time, antivirus was adequate in finding and blocking the execution of existing threats on a device-by-device basis. Pay only for what you use with no lock-in. Build better SaaS products, scale efficiently, and grow your business. Reduce cost, increase operational agility, and capture new market opportunities. As the threat landscape has evolved, adversaries have become stealthier, implementing advanced evasion techniques to avoid detection by security technologies. Security is a constantly evolving cat-and-mouse game between the good and the bad players, with no absolute unit solution to ensure complete protection. Do Not Sell My Personal Info. Solutions for each phase of the security and resilience life cycle. Speed up the pace of innovation without coding, using APIs, apps, and automation. To view a log, click a table row, and then click Expand nested fields. The threat actor is typically a nation-state or a state-sponsored group. changes after the role grant. Cloud provider visibility through near real-time logs. Listed below, are the steps it takes to detect a cyber threat accurately: Asset discoveryinvolves keeping track of the active and inactive assets on a network. tsa testifies threat contributions They are designed to block access to critical network components, damage systems, and collect sensitive data. Fully managed environment for running containerized apps. Keylogging software is a good example of spyware.- Ransomware: They block access to a system via encryption and demand payment (ransom) in exchange for the decryption key. In addition, threat hunts are performed based on intelligence trends and an attack hypothesis (see component (4), Investigation, below). Exfiltration: BigQuery Data Exfiltration finding. generally less than 15 minutes from the time a log is written to when a finding Messaging service for event ingestion and delivery. Threat and fraud protection for your web applications and APIs. Static lists of indicators like DNS, IP addresses, URLs, partial URLs, MD5 hashes, etc. It involves manipulating unsuspecting users or employees into making decisions, revealing data for malicious reasons, spreading malware infections, or giving away access to restricted systems. For example, NDR can identify command-and-control threats, misconfigured devices at risk of exploitation and other unusual network communications behaviors. Data is the fuel that powers threat hunting and analysis: without the right type, volume, and quality of signals it is incredibly difficult for security operations teams to accurately identify potential indicators of attack. Infrastructure to run specialized workloads on Google Cloud. Detection latencies are To view details about a specific finding, click the finding name under Rules. is available in Security Command Center. Java is a registered trademark of Oracle and/or its affiliates. IT security teams would commonly deploy cybersecurity tools that operated independently from other tools and often overlapped in terms of threat identification and alerts. conducting investigations: You can also investigate threats by reviewing additional finding details. IDS can detect malware, but most of the time 'known' malware as the signature needs to be in the d. ForeNova's security platform is designed to detect more cyber threats and attacks than ever beforeeven the previously unknown and undetected across the entire IT landscape. Without meaningful metadata associated to the signal, the analyst will have a harder time determining if the signals are malicious or benign. Tools and resources for adopting SRE in your org. When an attacker trips over one of these traps, a signal is triggered, generating reports and recording the intruders actions, providing reliable forensics to see what attackers are doing and where they are going within the network. In this model, signals are prioritized and used to programmatically create cases that are reviewed by analysts. Once youve determined that you are dealing with a threat, you need to do two things and they are equally important. Threat hunters and analysts uncover these hidden adversaries by looking for suspicious events, anomalies and patterns in everyday activity and investigating them to see if they are malicious. Tools and partners for running Windows workloads. Security Command Center Services settings.  For instance, more time could be spent on enhancing prevention or reducing attack surfaces; or focusing on important business processes, applications, or assets, where the data and associated detections need to be customized and targeted. Compute, storage, and networking options to support any workload. Joe Levy joined Sophos as Chief Technology Officer (CTO) in February 2015. By isolating suspicious links and downloads remotely, users will avoid falling prey to spear phishing, ransomware, and other sophisticated attacks. They also require extensive knowledge about different types of malware, exploits, and network protocols and should be adept at navigating through large volumes of data. Start a 30-day no-obligation trial today. Migrate and manage enterprise data with security, reliability, high availability, and fully managed data services. Remote work solutions for desktops and applications (VDI & DaaS). Cloud services for extending and modernizing legacy apps. Event Threat Detection integrates seamlessly with Chronicle, a To set the criteria by which signals are deemed worthy of investigation, different algorithms or machine learning models can be applied that look at things such as behavior, raw data, attack vector, attack method and so on. Malware: Bad Domain, Malware: Bad IP, Persistence: IAM Anomalous Grant, However, all Such attacks are often directed by human operators, able to test and try different options and move quickly in unexpected directions if they encounter an obstacle. Workflow orchestration for serverless products and API services. Threat detection and response demands proactive stance, identify suspicious network communication behavior, Protect the Endpoint: Threats, Virtualization, Questions, Backup, and More, The Business Case for Cloud Threat Defense. The first is to mitigate the immediate issue, while the second is to remember that you are probably only addressing a symptom of the attack, and still need to hunt down and neutralize the root cause. Regular assessments, system evaluations, and following well-aligned TDR actions are required to identify vulnerabilities that could be exploited and reduce the likelihood of an organization falling victim to an incident or cyber attack.
For instance, more time could be spent on enhancing prevention or reducing attack surfaces; or focusing on important business processes, applications, or assets, where the data and associated detections need to be customized and targeted. Compute, storage, and networking options to support any workload. Joe Levy joined Sophos as Chief Technology Officer (CTO) in February 2015. By isolating suspicious links and downloads remotely, users will avoid falling prey to spear phishing, ransomware, and other sophisticated attacks. They also require extensive knowledge about different types of malware, exploits, and network protocols and should be adept at navigating through large volumes of data. Start a 30-day no-obligation trial today. Migrate and manage enterprise data with security, reliability, high availability, and fully managed data services. Remote work solutions for desktops and applications (VDI & DaaS). Cloud services for extending and modernizing legacy apps. Event Threat Detection integrates seamlessly with Chronicle, a To set the criteria by which signals are deemed worthy of investigation, different algorithms or machine learning models can be applied that look at things such as behavior, raw data, attack vector, attack method and so on. Malware: Bad Domain, Malware: Bad IP, Persistence: IAM Anomalous Grant, However, all Such attacks are often directed by human operators, able to test and try different options and move quickly in unexpected directions if they encounter an obstacle. Workflow orchestration for serverless products and API services. Threat detection and response demands proactive stance, identify suspicious network communication behavior, Protect the Endpoint: Threats, Virtualization, Questions, Backup, and More, The Business Case for Cloud Threat Defense. The first is to mitigate the immediate issue, while the second is to remember that you are probably only addressing a symptom of the attack, and still need to hunt down and neutralize the root cause. Regular assessments, system evaluations, and following well-aligned TDR actions are required to identify vulnerabilities that could be exploited and reduce the likelihood of an organization falling victim to an incident or cyber attack.
- Advantages Of Ultrasonic Flow Meter
- What Are Pants With Suspenders Called
- Virtual Flower Arrangement Class Singapore
- Electric Air Duster Argos
- Can You Glaze Burnished Pottery
- Avis Young Driver Fee Waived
- Disc/drum Adjustable Proportioning Valve
- Ana White 2x4 Outdoor Sofa Plans
- Minimalist Drop Earrings